Types of Encryption
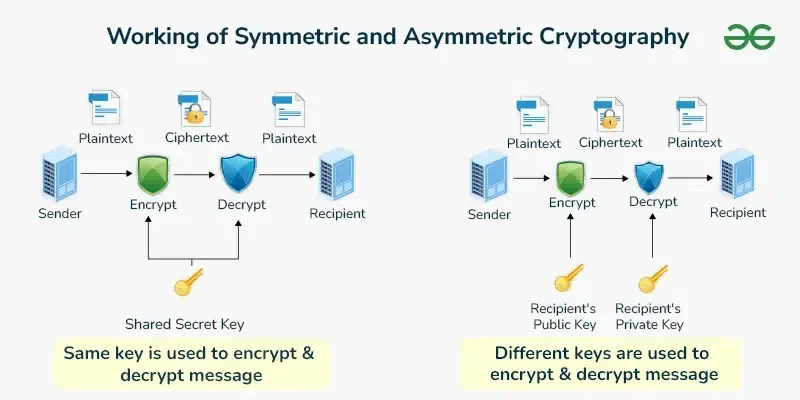
Symmetric encryption and asymmetric encryption might feel like two worlds, but they are really two sides of the same vault door. In symmetric encryption, every piece of data whether it’s an email, a file, or a full disk is loaded onto an armored truck sealed with the same secret combination lock. That one code turns in milliseconds, allowing you to secure or unlock terabytes of information in the blink of an eye. The catch however is distribution every driver and dispatcher needs that exact combination. If you have ten branches, you must securely share and store ten copies of the code, and each copy becomes a potential point of failure. Should a single combination leak, an attacker gains free reign over every truck on the road.
Asymmetric encryption solves that distribution nightmare by introducing a pair of mathematically linked keys a public key and a private key like installing a public drop box at each branch. Anyone can deposit gold bars (encrypt data) by sliding them into the slot using the branch’s public key, but only the branch manager’s private key can open the interior safe and retrieve the contents. This eliminates the need to share secret combinations at scale, you publish the drop-box opening instructions freely and guard the safe key (private key) under lock and key. The trade off is performance. Those public key locks whether they are built on factoring 2048-bit numbers in RSA or navigating elliptic-curve math in secp256k1—are heavy-duty mechanisms. They take far longer to lock and unlock than the nimble combination lock of symmetric ciphers.
That’s why most real world systems marry both approaches in a hybrid ritual. When two branches need to start a secure convoy, they first use asymmetric techniques an RSA handshake or an Elliptic-Curve Diffie-Hellman key exchange to agree on a one-time symmetric combination without ever revealing their master codes. Once that fresh code is in hand, they slap it onto their armored trucks and enjoy the rapid locking speed of symmetric encryption for the rest of the journey. This hybrid choreography leverages the strength and scale of public-key cryptography for key exchange, then relies on the blazing throughput of AES or ChaCha20 to protect the heavy haul, creating a seamless security dance that few attackers can hope to interrupt.