Red Stealer Lab — Threat Intelligence Walkthrough
Scenario Introduction
In this lab, I’m stepping into the role of a Threat Intelligence analyst inside a SOC. A suspicious executable was found on a colleague’s workstation, and it’s suspected of talking to a Command and Control (C2) server. My mission is to investigate this file by analyzing its SHA-256 hash, extract indicators of compromise (IOCs), identify techniques, and put together useful intelligence for the Incident Response team.
I started with only the hash. From there, I pivoted through VirusTotal, MalwareBazaar, and ThreatFox (linked to Malpedia) to answer nine key questions. At every step I explain what I did, where I would take screenshots, and why the finding matters.
Q1 — Malware Category
Question: “What category has Microsoft identified for that malware in VirusTotal?”
Investigation
I pasted the SHA-256 hash into VirusTotal’s search bar and opened the Summary tab. Scrolling to the Security vendors’ analysis section, I found Microsoft’s entry. Microsoft had it flagged as a Trojan.
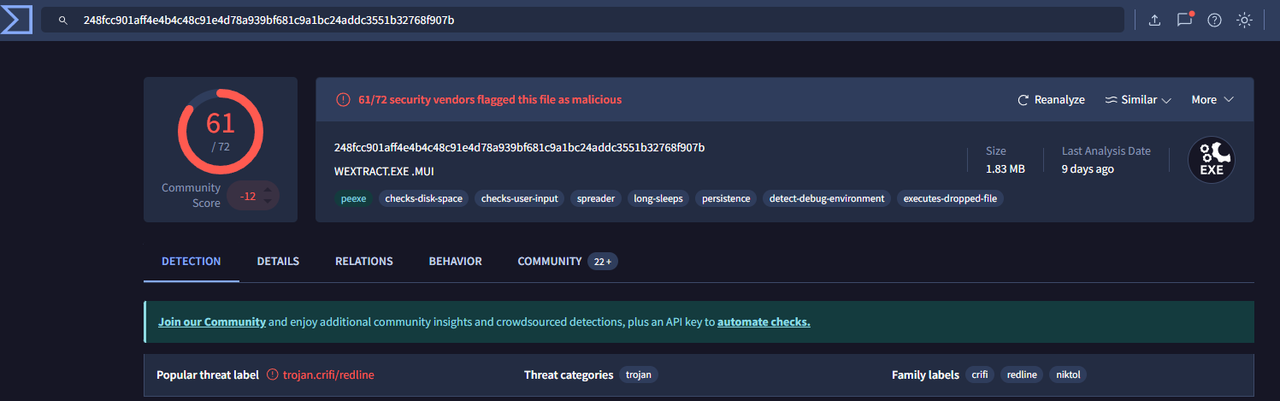
Answer: Trojan
By checking Microsoft’s classification in VirusTotal, I confirmed this file is a Trojan. That instantly gives me context: I’m likely dealing with something that disguises itself and phones home to a C2. It sets a different triage path compared to other categories like ransomware or spyware.
Q2 — File Name
Question: “What’s the file name associated with this malware? (Don’t include the extension.)”
Investigation
On VirusTotal’s Details tab, I scrolled down to the Names section. The malware was listed as wextract.exe. Since the question wanted no extension, the answer is simply wextract.
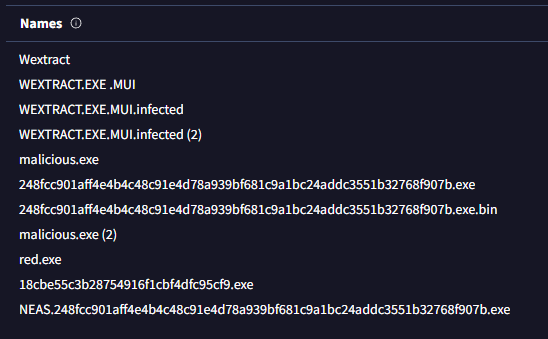
Answer: wextract
The malware tried to pass itself off as a legitimate Windows component. Knowing the filename is important because we can now pivot in EDR or log searches to see if this file appeared anywhere else in the environment.
Q3 — First Submission Timestamp
Question: “What is the UTC timestamp of the malware’s first submission to VirusTotal?”
Investigation
Still in the Details tab, I scrolled to the History section. The First Submission timestamp was 2023-10-06 04:41:50 UTC. For the lab format, I trimmed it to 2023-10-06 04:41 (UTC).
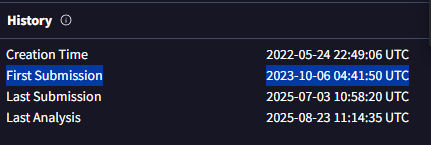
Answer: 2023-10-06 04:41 (UTC)
This tells me when the malware was first uploaded to VirusTotal. Since it’s fairly recent, that means detection coverage may still be maturing, and our SOC should treat it with higher urgency.
Q4 — MITRE ATT&CK Technique
Question: “What is the MITRE ATT&CK technique ID for the malware's data collection from the system before exfiltration?”
Investigation
In the Behavior tab of VirusTotal, I scrolled down to the MITRE ATT&CK mapping section. Under the Collection tactic, the malware was mapped to T1005 — Data from Local System.
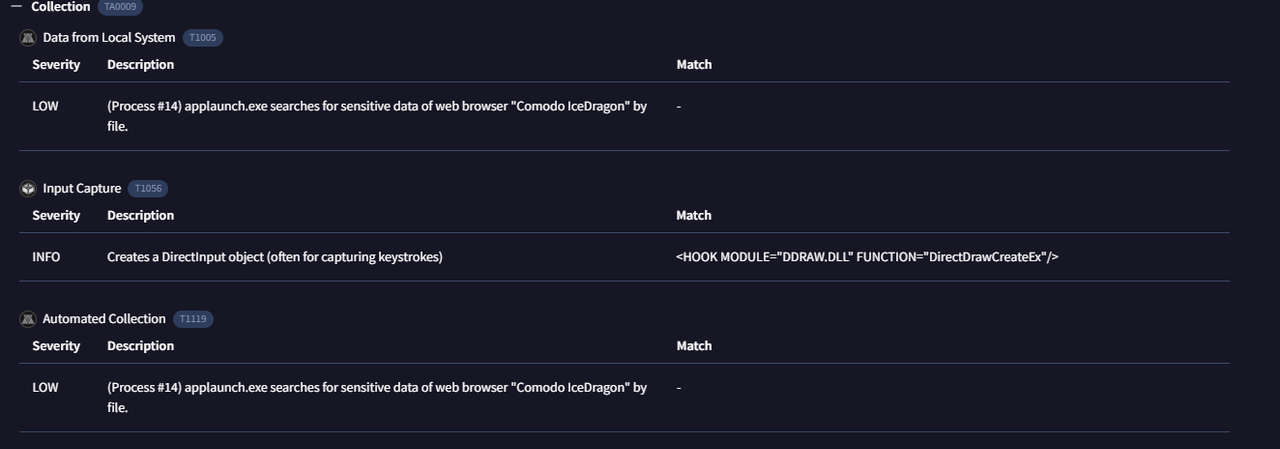
Answer: T1005 — Data from Local System
Mapping this behavior to MITRE gives defenders a standard reference point. It confirms the malware collects files locally before sending them out — exactly the kind of thing we’d want to monitor for in EDR rules.
Q5 — Domain Resolution
Question: “Which social media-related domain names did the malware resolve via DNS queries?”
Investigation
Also under the Behavior tab, I looked at the DNS resolution section. Among the resolved domains, I saw facebook.com and related subdomains.
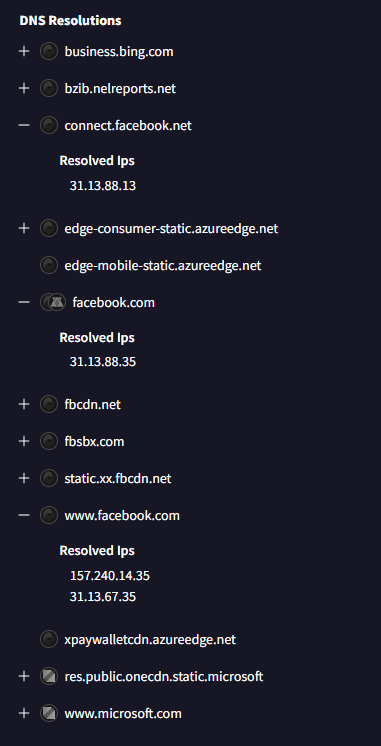
Answer: facebook.com
The malware hides in plain sight by mixing in requests to Facebook. Because Facebook is a trusted domain, its traffic usually doesn’t raise alarms. This is a clever evasion technique, and one defenders need to be aware of.
Q6 — Malicious IP and Port
Question: “Can you provide the IP address and destination port the malware communicates with?”
Investigation
Scrolling further in the Behavior tab, I found the IP Traffic section. One entry stood out: 77.91.124.55:19071.
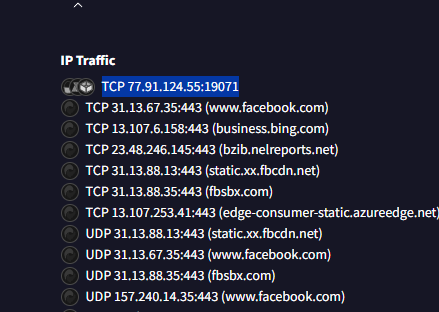
Answer: 77.91.124.55:19071
This is a critical IOC — the C2 server and its port. With this, the SOC can block it at the firewall, add detections in IDS, and query logs to see if any other machines made this connection.
Q7 — YARA Rule
Question: “Using MalwareBazaar, what’s the name of the YARA rule created by ‘Varp0s’ that detects the identified malware?”
Context
VirusTotal doesn’t provide community-contributed YARA rules, so I pivoted to MalwareBazaar, which specializes in sample sharing and YARA intel.
Investigation
On MalwareBazaar (https://bazaar.abuse.ch/), I searched the SHA-256 hash. On the sample page, I opened the YARA tab and found the rule authored by Varp0s: detect_Redline_Stealer.
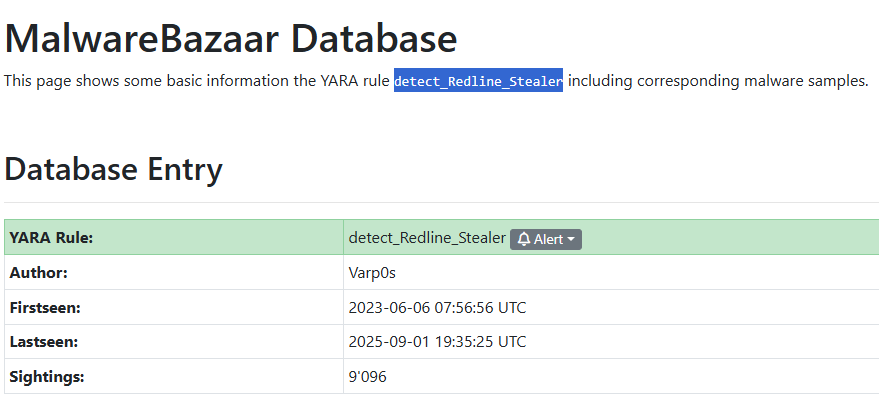
Answer: detect_Redline_Stealer
Community YARA rules are powerful because they let us hunt across mail attachments, file servers, or even memory dumps. Having this rule already available speeds up detection engineering.
Q8 — Malware Alias
Question: “Can you provide the different malware alias associated with the malicious IP address according to ThreatFox?”
Context
MalwareBazaar doesn’t give aliases. For that, I used ThreatFox, which tracks IPs, domains, and families. From ThreatFox, I pivoted to Malpedia to confirm the alias.
Investigation
On ThreatFox (https://threatfox.abuse.ch/), I searched for malware:Redline. In the results, I clicked the RedLine Stealer family entry and followed the link to Malpedia. The Malpedia family page listed the alias as RECORDSTEALER.
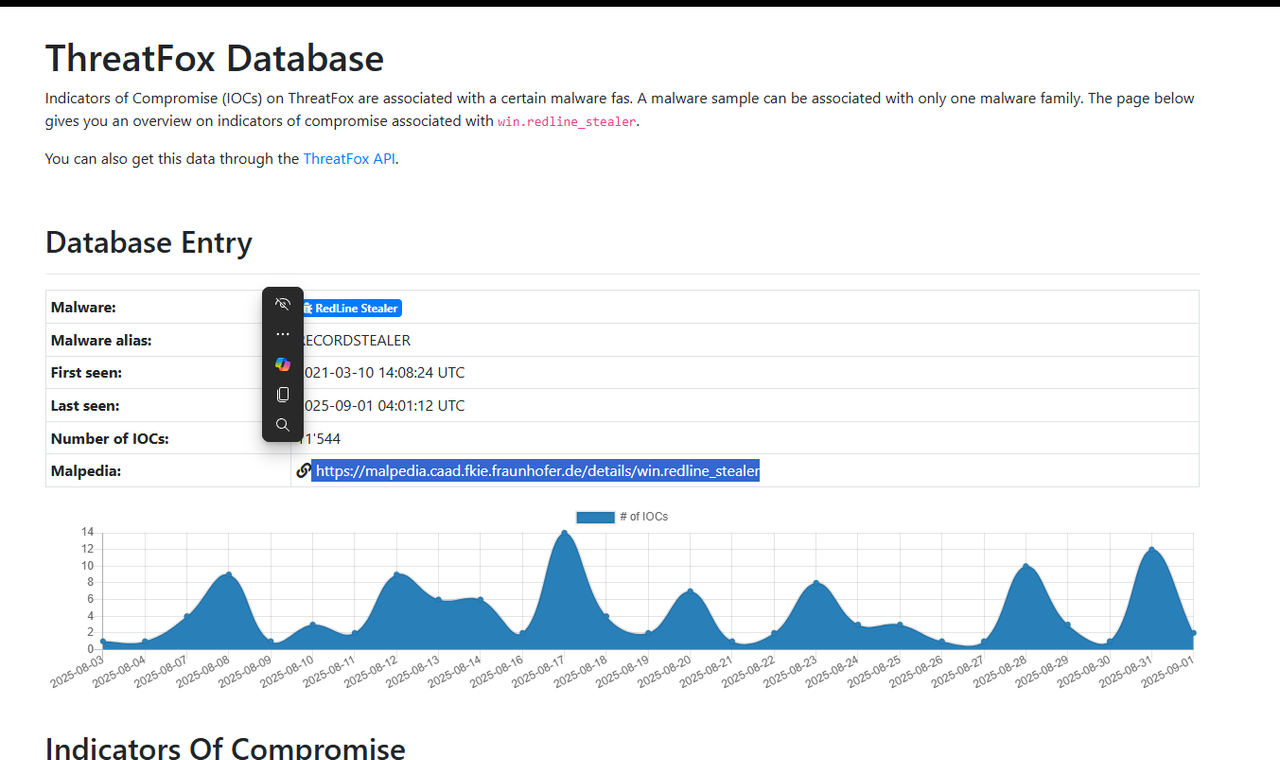
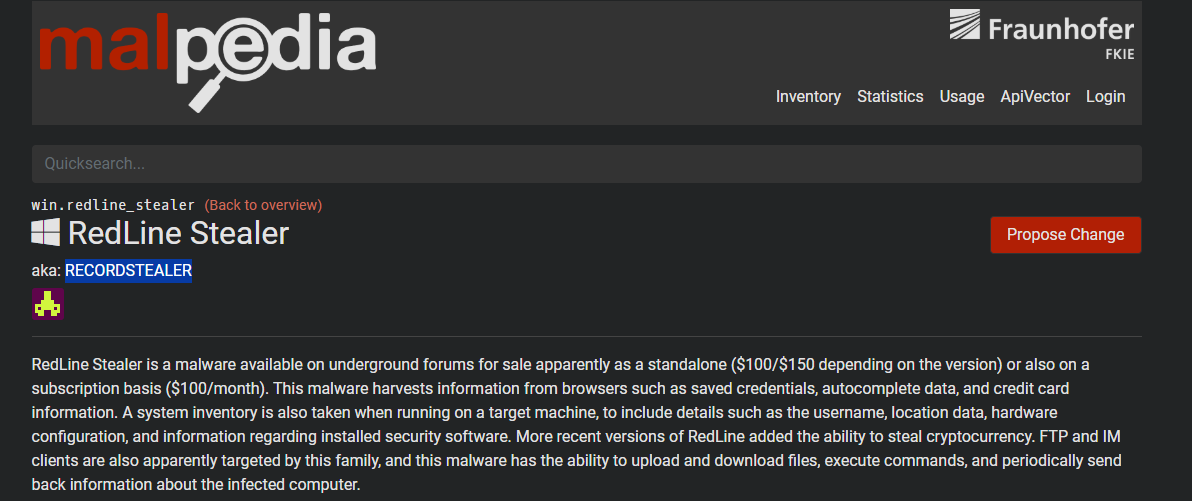
Answer: RECORDSTEALER
Recording RECORDSTEALER makes sure our SOC doesn’t miss intel just because it’s labeled differently in another tool.
Q9 — Imported DLL
Question: “Can you provide the DLL utilized by the malware for privilege escalation?”
Investigation
Back in VirusTotal, I opened the Details tab and scrolled to the Imports section. There I found ADVAPI32.dll, which is known for functions like AdjustTokenPrivileges that are often abused for privilege escalation.
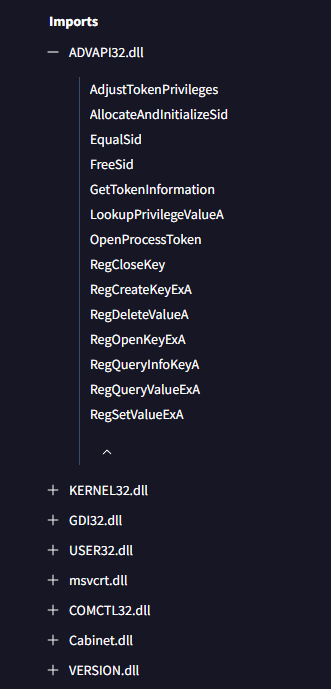
Answer: ADVAPI32.dll
The malware uses ADVAPI32.dll to manipulate Windows access tokens, which allows it to escalate privileges. This is something defenders can monitor — unusual calls to these functions by suspicious processes should be a red flag.
Final Wrap-Up
Starting with only a SHA-256 hash, I built a full profile of the malware. VirusTotal gave me the basics — Trojan category, filename wextract, first-seen date, MITRE T1005, DNS queries to facebook.com, and a C2 at 77.91.124.55:19071.
When VirusTotal wasn’t enough, I pivoted: MalwareBazaar gave me the YARA rule (detect_Redline_Stealer), and ThreatFox > Malpedia gave me the alias (RECORDSTEALER). Finally, I confirmed the malware imports ADVAPI32.dll to escalate privileges.
This is exactly how I’d work in a SOC: start with a single IOC, pivot across trusted sources, and package the findings into actionable intelligence.