Malware Hash Investigation Walkthrough
During a regular IT security check at GlobalTech Industries, abnormal network traffic was detected from multiple workstations. Employees reported that their search queries were being redirected to suspicious websites. Our SOC team was tasked with investigating. We were provided with the following SHA-256 hash to begin analysis:
30E527E45F50D2BA82865C5679A6FA998EE0A1755361AB016739508100071C85The following lab is my investigation process and answers to each of the questions.
Q1: What is the name of the malware family that causes abnormal network traffic?
Step 1 – Verify the hash type
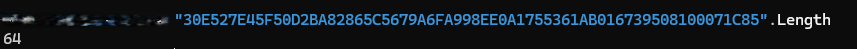
On my Windows 11 host, I used PowerShell to check the length of the hash string:
"30E527E45F50D2BA82865C5679A6FA998EE0A1755361AB016739508100071C85".LengthThe result was 64, confirming that this is a SHA-256 hash.
Step 2 – Search LevelBlue Labs
When I checked VirusTotal, no hits appeared at first. So I pivoted to LevelBlue Labs (formerly AlienVault OTX), entered the SHA-256, and got a match. From there, I pivoted back to VirusTotal and found the malware labeled consistently.
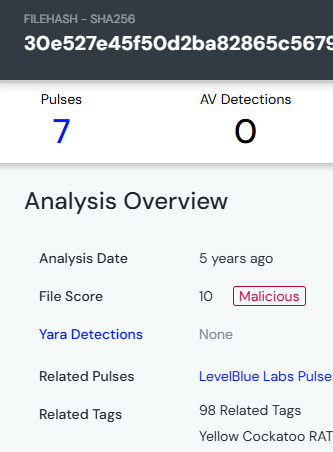
The malware family was identified as Yellow Cockatoo RAT.
RATs (Remote Access Trojans) like Yellow Cockatoo allow attackers to hijack infected systems remotely. This matched what GlobalTech observed — abnormal traffic and redirections. Identifying the family gave us a baseline for hunting further IOCs.
Answer to Q1:
Yellow Cockatoo RATQ2: What is the common filename associated with the malware discovered on our workstations?
Step 1 – VirusTotal “Details” Tab
With the hash loaded in VirusTotal, I checked the Details tab. Here I found the filename metadata tied to the sample:
111bc461-1ca8-43c6-97ed-911e0e69dfd8.dll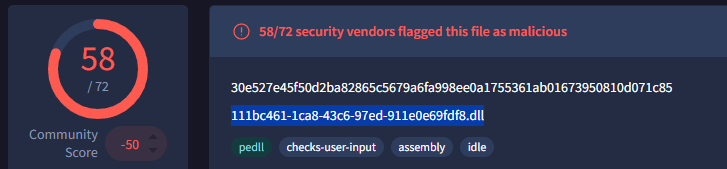
RATs often hide behind long GUID-like filenames. To a casual eye, this looks like a random system file. But by correlating this IOC, defenders can query across enterprise endpoints to find compromised machines.
Answer to Q2:
111bc461-1ca8-43c6-97ed-911e0e69dfd8.dllQ3: What is the compilation timestamp of the malware that infected our network?
Step 1 – VirusTotal “History” Section
Still inside VirusTotal, I reviewed the History section. The “Creation Time” field shows when the binary was compiled.
2020-09-24 18:26:47 UTC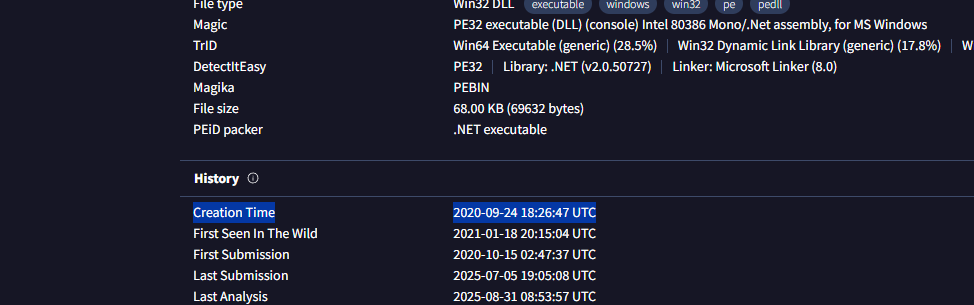
This tells us the malware was built in September 2020. Since the first submission was in October 2020, defenders spotted it quickly. This helps us judge how long attackers may have been using this variant before it hit the wild.
Answer to Q3:
2020-09-24 18:26:47 UTCQ4: When was the malware first submitted to VirusTotal?
Step 1 – Review History in VirusTotal
From the same History panel, I noted the First Submission field:
2020-10-15 02:47:37 UTC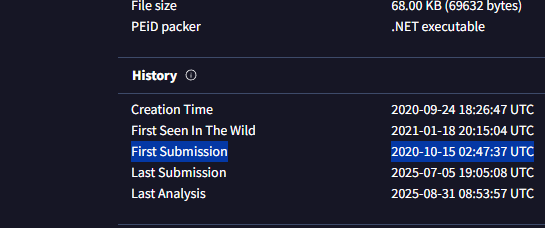
Comparing compilation time (September 2020) to first submission (October 2020) gives us ~3 weeks of undetected activity before wider visibility. This is valuable context for incident response timelines.
Answer to Q4:
2020-10-15 02:47:37 UTCQ5: What is the name of the .dat file that the malware dropped in the AppData folder?
Step 1 – Checking VirusTotal Relations Tab
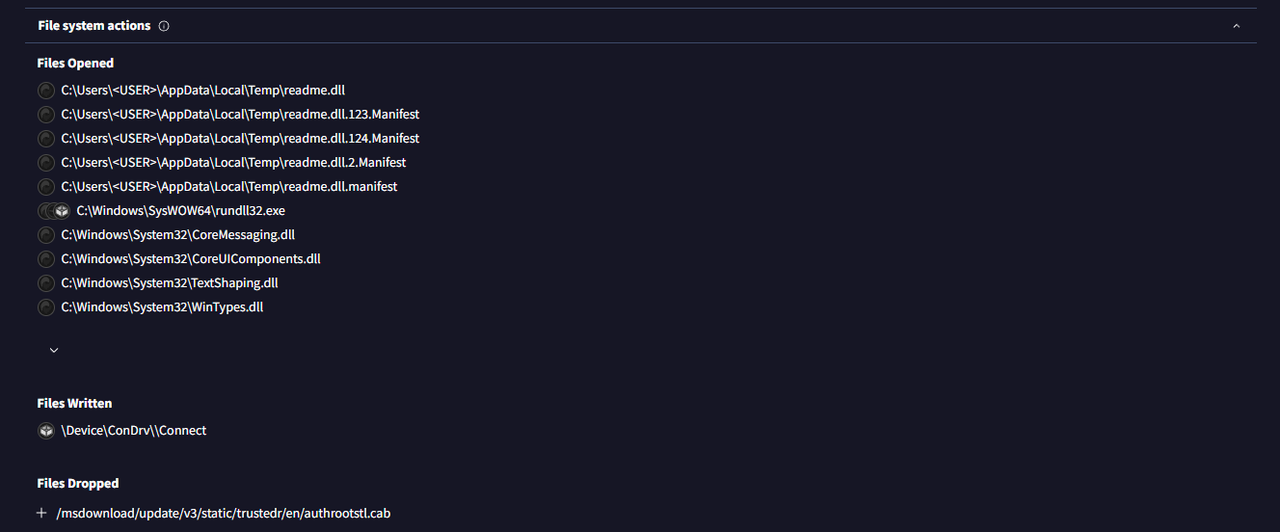
I checked VirusTotal’s Relations > Dropped Files, but only found a CAB file (authrootstl.cab). No .dat file appeared.
Step 2 – Pivoting to Red Canary
Because VirusTotal didn’t show it, I pivoted to Red Canary’s intel report on this hash.By just pasting the hash into the URL and that populated the report I needed. There, I found the missing artifact:
%USERPROFILE%\AppData\Roaming\solarmarker.dat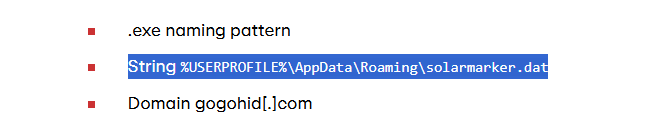
This persistence file is an excellent IOC. Even if the main DLL changes names, the RAT still needs its solarmarker.dat config file in AppData. SOC analysts can hunt for this file across systems to detect infections.
Answer to Q5:
solarmarker.dat(Path: %USERPROFILE%\AppData\Roaming\solarmarker.dat)
Q6: What is the C2 server that the malware is communicating with?
Step 1 – Red Canary Network IOCs
From the same Red Canary report, I identified the C2 domain used by this RAT:
gogohid.com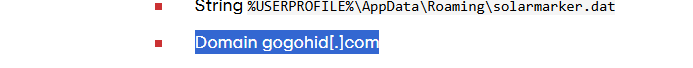
Blocking this domain at firewalls, proxies, and DNS layers immediately severs the attacker’s remote control. This step is critical for containment, even before cleaning every infected machine.
Answer to Q6:
gogohid.comFinal Report Summary
In this investigation, we analyzed the malware sample with SHA-256 hash:
30E527E45F50D2BA82865C5679A6FA998EE0A1755361AB016739508100071C85Using a combination of LevelBlue Labs, VirusTotal, and Red Canary, we uncovered the following:
- Malware Family: Yellow Cockatoo RAT (a Remote Access Trojan).
- Filename:
111bc461-1ca8-43c6-97ed-911e0e69dfd8.dll. - Compilation Time: 2020-09-24 18:26:47 UTC.
- First Submission to VirusTotal: 2020-10-15 02:47:37 UTC.
- Dropped File:
solarmarker.datin%USERPROFILE%\AppData\Roaming\. - C2 Domain:
gogohid.com.
How we found it:
We confirmed the hash format in PowerShell, pivoted between multiple threat intel platforms, and combined sandbox data with community OSINT (Red Canary) to fill gaps. Each pivot gave us new IOCs — from filenames to config files to network indicators.
Why it matters:
This RAT provides attackers with remote access and exfiltration capabilities. By identifying the family, artifacts, and C2 infrastructure, GlobalTech’s SOC can now:
- Block the C2 domain (
gogohid.com). - Hunt for the dropped DLL and
.datfile across all endpoints. - Understand the historical timeline (compiled in 2020, first seen in VirusTotal a few weeks later).
Framework Mapping:
MITRE ATT&CK:
- T1105 – Ingress Tool Transfer
- T1071 – Application Layer Protocol (C2 over HTTP/S)
- T1055 – Process Injection
- T1547 – Boot or Logon Autostart Execution (AppData persistence)
NIST CSF:
- Detect (DE.AE-1, DE.AE-2): Analyze anomalies and detect malware activity.
- Respond (RS.AN-1, RS.MI-1): Identify indicators and block C2.
- Protect (PR.AC-1): Restrict execution of malicious files in user directories.
This investigation shows how layering tools (VirusTotal, LevelBlue Labs, Red Canary) helps close intelligence gaps and provides defenders with a complete IOC package for containment and eradication.